See below for adding an external root Certificate Authority (CA) – that is, a root Certificate Authority created outside the Certificate Authority solution.
The following steps will ask you to have the certificate of this external CA at hand.
To add an external root Certificate Authority
Open the following URL in a Web browser.
https://<machine>/management-consoleWhere
<machine>is the IP address or domain name of the machine hosting PKI Hub.- Log in to the Management Console as one of the users created in Creating Certificate Authority tenants. This user will be the tenant of the new root external Certificate Authority.
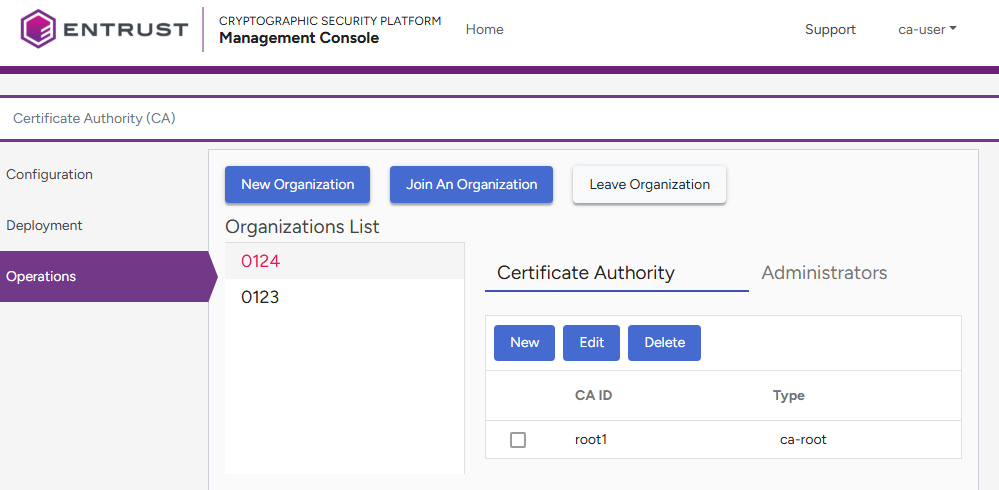
- In the content pane, click Manage Solution under Certificate Authority (CA).
- Select Operations in the sidebar.
- Select an organization under Organizations list.
See Managing organizations for how to create or join an organization.
- Click New under Certificate Authority.
- Configure the following settings.
- Click Submit to create the new Certificate Authority.
CA Type
Click External Root Certificate Authority.
Mandatory: Yes.
CA Identifier
Type a unique identifier for the new Certificate Authority within its organization. This identifier:
- Must be 3-18 characters long.
- Can only include lowercase letters, numbers, underscores ("_"), and hyphens ("-").
Do not reuse the identifier of a Certificate Authority for up to 24 hours after it has been deleted.
Mandatory: Yes.
Friendly Name
A friendly name for the new Certificate Authority in the user interface.
Mandatory: No. This optional value defaults to the one assigned to the CA Identifier field.
Self-Signed Root Certificate
Paste the PEM-encoded certificate signing certificate of the external CA – for example:
-----BEGIN CERTIFICATE-----MIIEKjCCAxKgAwIBAgIEOGPe+DANBgkqhkiG9w0BAQUFADCBtDEUMBIGA1UEChMLRW50cnVzdC5uZXQxQDA+BgNVBAsUN3d3dy5lbnRydXN0Lm5ldC9DUFNfMjA0OCBpbmNvcnAuIGJ5IHJlZi4gKGxpbWl0cyBsaWFiLikxJTAjBgNVBAsTHChjKSAxOTk5IEVudHJ1c3QubmV0IExpbWl0ZWQxMzAxBgNV...zX1XEC+bBAlahLVu2B064dae0Wx5XnkcFMXj0EyTO2U87d89vqbllRrDtRnDvV5bu/8j72gZyxKTJ1wDLW8w0B62GqzeWvfRqqgnpv55gcR5mTNXuhKwqeBCbJPKVt7+bYQLCIt+jerXmCHG8+c8eS9enNFMFY3h7CI3zJpDC5fcgJCNs2ebb0gIFVbPv/ErfF6adulZkMV8gzURZVE=-----END CERTIFICATE-----Mandatory: Yes.